Import Redistributables into Microsoft Intune¶
Import-VcIntuneApplication automates packaging and importing Visual C++ Redistributables as Win32 applications into Microsoft Intune. Each redistributable is packaged, assigned detection and requirement rules, and imported as a separate application.
Key features: - Packages each Visual C++ Redistributable as a .intunewin file - Sets application properties: Name, Description, Publisher, Version, URLs, Notes, Logo, Install/Uninstall commands, Install behavior, OS architecture, minimum OS, detection and requirement rules - Skips import if the app already exists and is up-to-date in Intune - Cleans up temporary files after import
Note: - Requires the IntuneWin32App PowerShell module - Supported only on Windows PowerShell (not PowerShell Core) - Authenticate to Intune with
Connect-MSIntuneGraphbefore use - Requires a valid Microsoft Graph API access token
Initial Setup¶
To import the Visual C++ Redistributables into Microsoft Intune, some initial setup is required - first, install the required modules from the PowerShell Gallery:
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
Install-Module -Name VcRedist, IntuneWin32App, MSAL.PS
Parameters¶
VcList(required): An array of Visual C++ Redistributable objects, typically fromSave-VcRedist. Each object must have required properties (see below).
Prerequisites¶
- Install required modules:
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
Install-Module -Name VcRedist, IntuneWin32App, MSAL.PS
- Authenticate to Intune:
Connect-MSIntuneGraph -TenantID contoso.onmicrosoft.com
For non-interactive authentication, use an Entra ID app registration with DeviceManagementApps.ReadWrite.All permission:
Connect-MSIntuneGraph -TenantID contoso.onmicrosoft.com -ClientId "<appId>" -ClientSecret <secret>
- Ensure the IntuneWin32App module is available and a valid Microsoft Graph API access token is present.
Required VcList Properties¶
Each object in VcList must include:
Name,Version,Path,Architecture,SilentInstall,SilentUninstall,PackageId,URI, and other properties as produced bySave-VcRedist.
The function will validate these properties and throw if any are missing.
Authentication¶
Non-interactive Authentication¶
An Entra ID app registration can be used for non-interactive authentication. The app registration requires the DeviceManagementApps.ReadWrite.All application permission. Create an app registration, assign the permission and enable admin consent. Then use a client secret or client certificate to use with authentication.
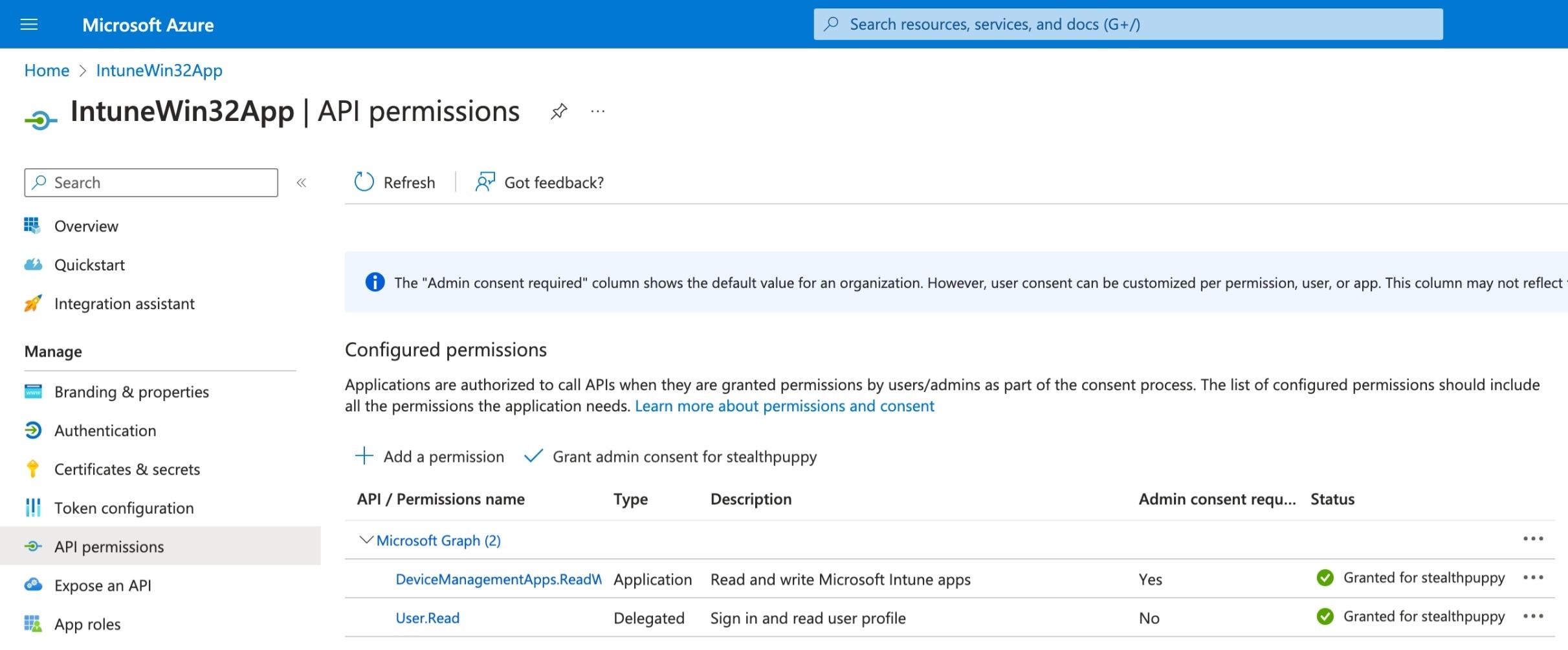
For a non-interactive sign-in that uses the app registration and a client secret, use this example:
Connect-MSIntuneGraph -TenantID contoso.onmicrosoft.com -ClientId "f99877d5-f757-438e-b12b-d905b00ea6f3" -ClientSecret <secret>
Example: Import Redistributables¶
The following example retrieves the list of Visual C++ Redistributables for the 2022 release, downloads the installers, and imports each as a Win32 app into Intune:
$VcList = Get-VcList -Release "2022" | Save-VcRedist -Path C:\Temp\VcRedist
Import-VcIntuneApplication -VcList $VcList
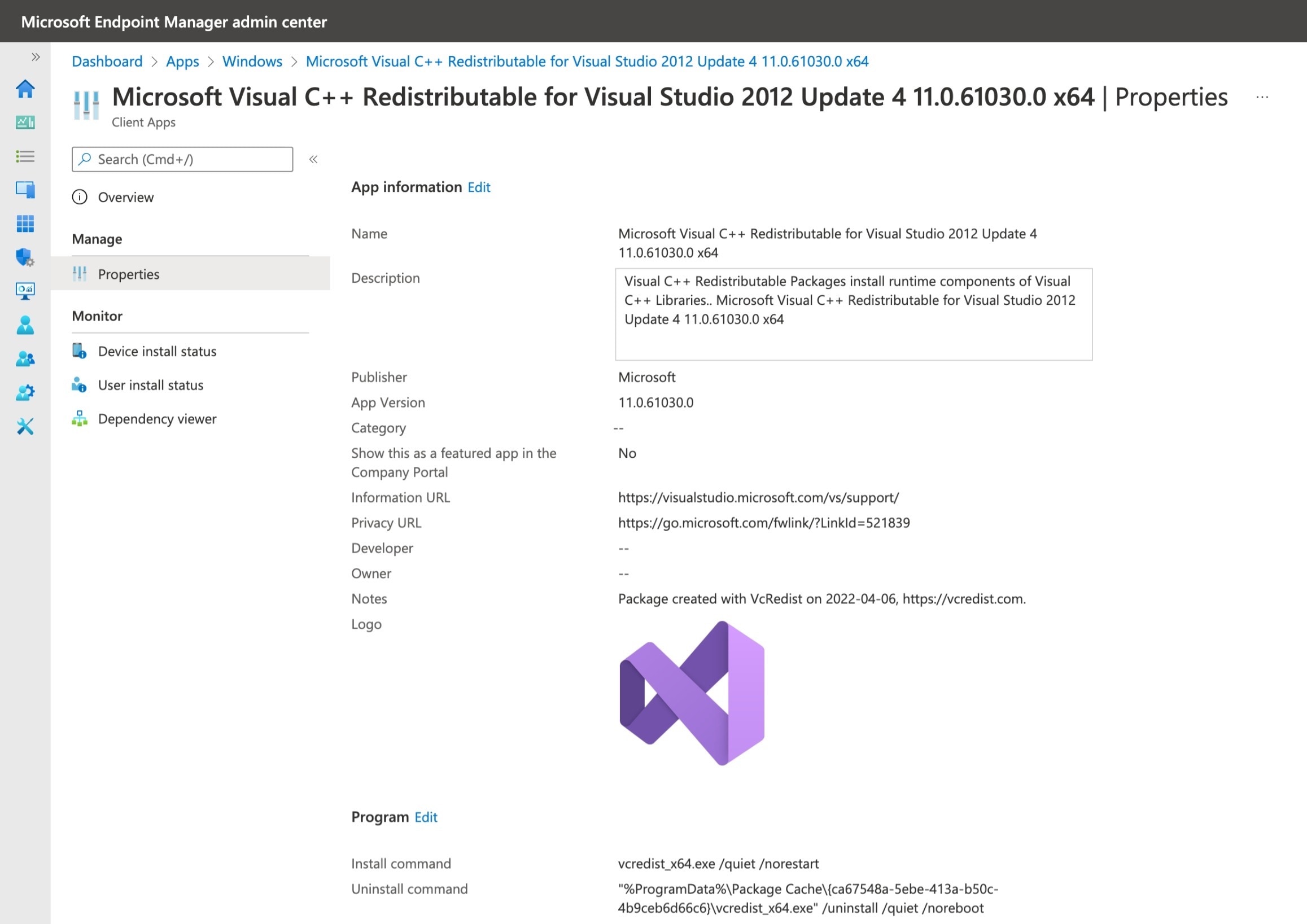
Application Assignments and Supersedence¶
After import, assign the applications using Add-IntuneWin32AppAssignmentAllDevices. The function returns application objects with an Id property:
# Retrieve existing Visual C++ Redistributable applications in Intune (that have been imported by VcRedist)
$ExistingApps = Get-VcIntuneApplication
# Import the new Visual C++ Redistributable versions
$NewApps = Get-VcList | Save-VcRedist -Path "C:\Temp\VcRedist" | Import-VcIntuneApplication
# Create an All Devices assignment and add supersedence rules for existing versions
foreach ($App in $NewApps) {
$params = @{
Id = $App.id
Intent = "required"
Notification = "showReboot"
DeliveryOptimizationPriority = "notConfigured"
UseLocalTime = $true
AvailableTime = $(Get-Date -Hour 18 -Minute 0 -Second 0)
DeadlineTime = $(Get-Date -Hour 18 -Minute 0 -Second 0).AddDays(1)
EnableRestartGracePeriod = $true
RestartGracePeriod = 1440
RestartNotificationSnooze = 240
RestartCountDownDisplay = 15
}
Add-IntuneWin32AppAssignmentAllDevices @params
# Match existing app packages with the same identifier and add supersedence rules
$MatchingApp = $ExistingApps | Where-Object { $_.PackageId -eq $($App.notes | ConvertFrom-Json -ErrorAction "Stop").Guid }
if ($null -ne $MatchingApp) {
foreach ($Item in $MatchingApp) {
Write-Host "Adding supersedence rule for $($Item.id) to $($App.id)"
$SupersedenceRule = New-IntuneWin32AppSupersedence -ID $Item.id -SupersedenceType 'Update'
Add-IntuneWin32AppSupersedence -ID $App.id -Supersedence $SupersedenceRule
}
}
}
How It Works¶
- Validates prerequisites:
- Ensures running on Windows PowerShell (not Core)
- Checks for IntuneWin32App module
- Checks for Microsoft Graph API access token
- Loads the Intune app manifest from
Intune.jsonin the module directory - Creates an icon object if the icon file exists
- Validates each VcList object for required properties
- Checks for existing Intune apps and skips import if up-to-date
- Packages the installer as a .intunewin file
- Creates requirement and detection rules from the manifest and VcList
- Imports the app using
Add-IntuneWin32App - Cleans up temporary files
Troubleshooting¶
- PowerShell Core not supported: The function will throw if run on PowerShell Core. Use Windows PowerShell 5.1.
- Missing modules: Ensure
IntuneWin32Appis installed and available in your session. - Authentication errors: Authenticate with
Connect-MSIntuneGraphand ensure$Global:AccessTokenis set. - Missing required properties: Use
Save-VcRedistto generate a validVcList.